The need for robust security measures is more important than ever. One such measure is using OTP (One-Time Password) tokens, which rely on hardware-based technology to enhance security.
We will explore the world of OTP token technology, its role in enhancing security, and how it effectively safeguards your digital assets.
What are OTP Tokens?
OTP tokens, or one-time password tokens, are small hardware devices or applications that generate unique passwords for one-time use. These passwords are typically six to eight digits long and change after a short period, typically 30 seconds.
The primary purpose of OTP tokens is to provide an additional layer of security when accessing sensitive information, systems, or accounts.
How OTP Token Technology Works
OTP tokens work on a simple yet powerful concept. They generate time-based or event-based one-time passwords that are required for authentication. The following are the two main types of OTP tokens:
Time-Based OTP Tokens
Time-based OTP tokens generate passwords that are valid for a short duration, typically 30 seconds.
The device’s internal and server clocks must be synchronized to ensure successful authentication. This synchronization prevents replay attacks, where an attacker uses a previously captured OTP.
Event-Based OTP Tokens
Event-based OTP tokens generate passwords responding to a specific event, such as a button press on the hardware token device. The generated password is a unique response to the event and is only valid for a single use.
This method is highly secure as it’s not dependent on time and doesn’t require clock synchronization.
Enhancing Security with OTP Tokens
OTP tokens offer several security advantages:
Two-factor authentication (2FA)
OTP tokens are often a second factor in a two-factor authentication methods (2FA). To access a system or account, users must provide their regular password (something they know) and the OTP generated by the token (something they have).
This combination significantly enhances security, as even if attackers discover the regular password, they won’t have the OTP token
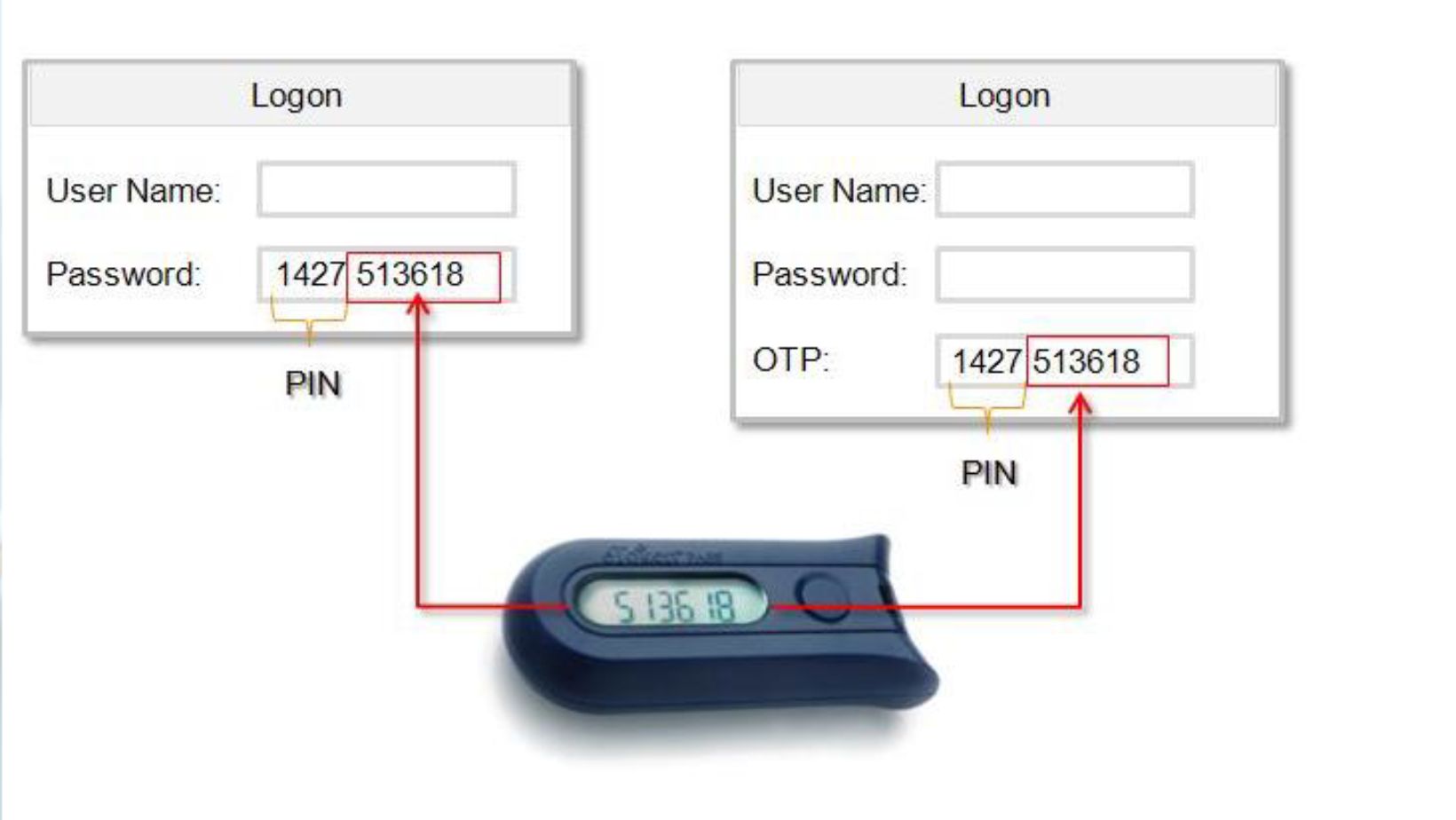
.
Protection against Phishing
Phishing attacks often trick users into revealing their login credentials. However, OTP tokens create an additional layer of security by ensuring that even if a user’s password is compromised, the attacker still won’t be able to access the account without the OTP token.
Mitigating Man-in-the-Middle Attacks
In a man-in-the-middle attack, an attacker intercepts communication between two parties and can manipulate or eavesdrop on the conversation.
OTP tokens mitigate this threat by providing unique, time-sensitive passwords that change frequently, making it nearly impossible for attackers to access sensitive data.
Benefits of Hardware-Based OTP Tokens
Hardware-based OTP tokens offer several advantages over their software-based counterparts:
Immunity to Malware
Software-based OTP tokens are vulnerable to malware attacks, as attackers can compromise the software on a user’s device.
Hardware-based tokens are immune to such attacks, as they are stand-alone devices that don’t rely on the security of the user’s computer or smartphone.
Durability and Longevity
Hardware tokens are typically built to last. They are designed to withstand physical wear and tear, ensuring they remain operational for a long time. In contrast, software-based tokens may become obsolete or require frequent updates.
Ease of Use
Hardware tokens are user-friendly and don’t require an internet connection or a specific operating system. Users can press a button or scan a barcode to generate the OTP, making them accessible to many users.
Everyday Use Cases for OTP Tokens
OTP tokens find applications in various sectors, including:
Online Banking
Banks often use OTP tokens to secure online banking transactions and ensure only authorized users can access their accounts.

Enterprise Security
Many organizations implement OTP tokens to protect their internal networks, systems, and confidential data from unauthorized access.
VPN and Remote Access
OTP tokens are commonly used to secure remote access to corporate networks and sensitive information, ensuring remote employees can connect to company resources safely.
E-commerce
E-commerce platforms use OTP tokens to secure customer accounts and verify transactions, reducing the risk of fraudulent activities.
Conclusion
OTP token technology is a robust and effective way to enhance security through hardware. By generating one-time passwords, OTP tokens provide additional protection against various online threats, including phishing, malware, and man-in-the-middle attacks.
The use of hardware-based OTP tokens ensures durability, immunity to malware, and ease of use, making them a practical and secure choice for organizations and individuals alike.
Investing in OTP token technology is a prudent step toward safeguarding your digital assets in today’s interconnected world as cyber threats continue to evolve.


