What is a DOD Public Key
The Department of Defense (DoD) uses a unique form of Public Key Infrastructure (PKI) to protect their digital networks. We refer to it as the DoD Public Key. Acting like a digital passport, it verifies and authenticates digital identities. Authentication, integrity, and non-repudiation – these key advantages are the cornerstone of the DoD PKI. Non-repudiation ensures every transaction is permanent and undeniable.
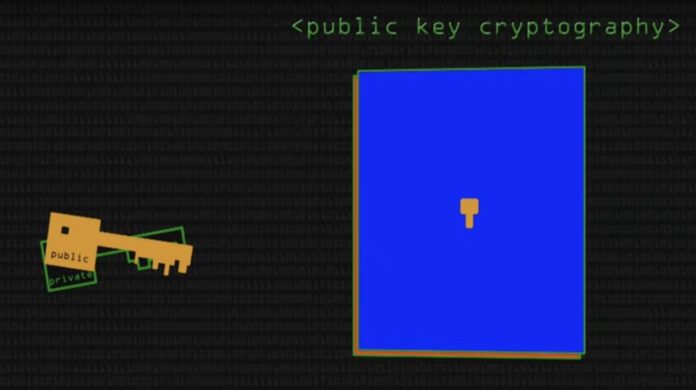
In this system, two keys are involved:
- A Private Key kept secret by the user
- A Public Key available to everyone in the network
The functioning of the keys is crucial as the private key is used to encrypt messages, whilst the public key decrypts them. This maintains the confidentiality of the information being shared.
However, no security system is foolproof. Despite its many advantages, there’s always a risk involved with using a DoD public key. It may be susceptible to key-compromise impersonation attacks or put users at risk if the key management isn’t perfected, or through a variety of other potential vulnerabilities within the network.
Data protection is not something we can compromise on, and understanding the intricacies of digital security systems such as the DoD PKI is a step towards achieving it. The DoD public key is an important defense tool in the digital world, and it’s critical to understand its strengths and potential drawbacks. With the right awareness and management, we can harness its benefits to its full potential.
Which of the Following is True of Using a DOD Public Key Infrastructure
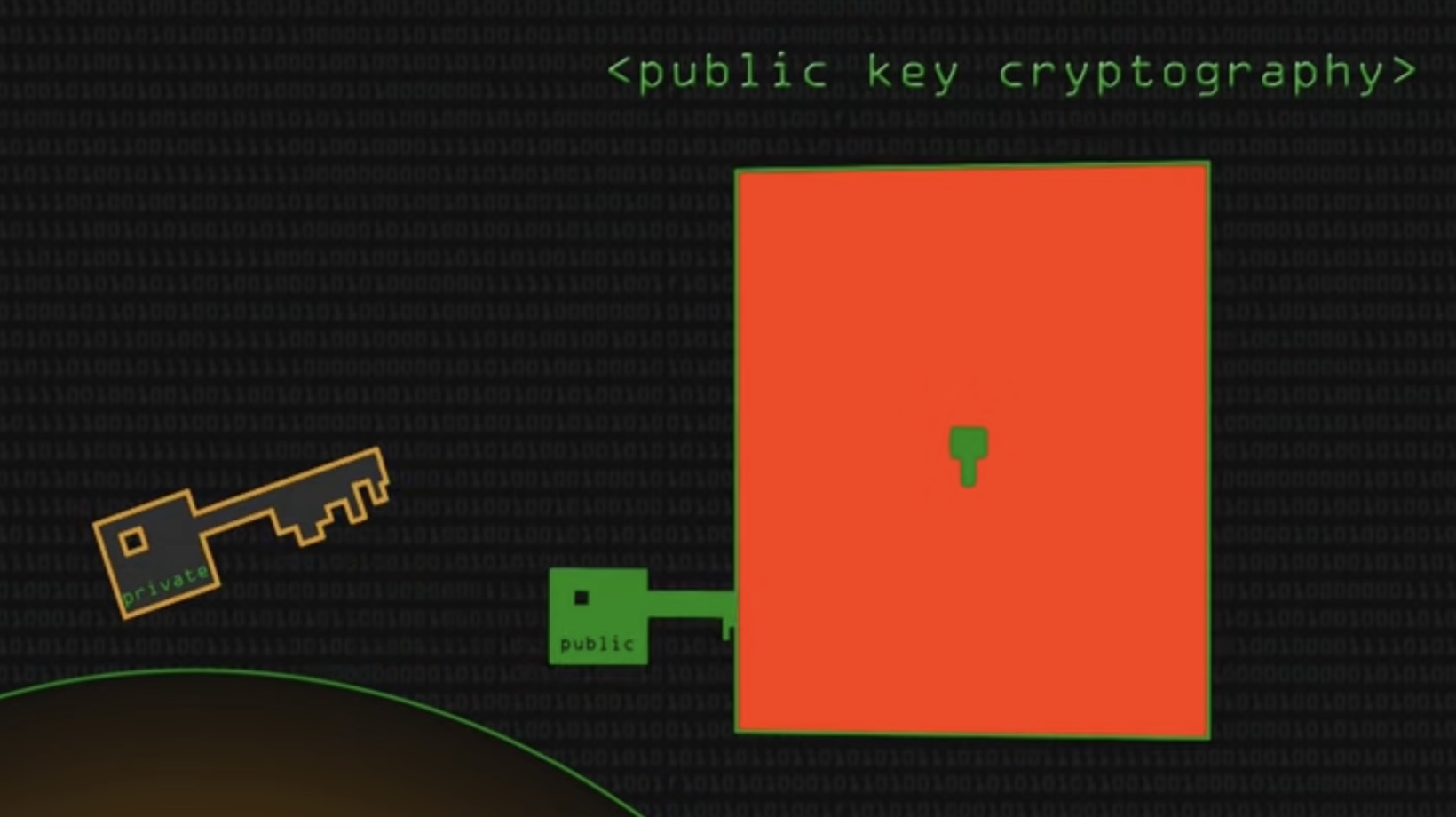
Using the Department of Defense (DoD) Public Key Infrastructure (PKI) comes with a number of advantages. Leveraging this tool, you could enjoy secure communications, thorough authentication, and trust-building digital signatures.
Enhanced Security
Security – it’s the backbone of any digital platform or network. By utilizing the DoD PKI, we reinforce our digital walls against potential attacks. The unique blend of a private key, for encryption and a public key for decryption ensures the concealment of sensitive information. Even if a breach of the network occurs, the confidential data is encrypted, making it harder to decipher.
The DoD PKI also provides protection against possible Man-in-the-Middle (MitM) attacks. In such scenarios, the perpetrator intercepts the communication between two parties. As the data transmitted via DoD PKI is encrypted, the intercepted information would be virtually useless in the hands of an unauthorized entity.
Authentication and Verification
The DoD Public Key does not only secure our communications but also solidifies our identity verification process. With PKI, we can authenticate the participating entities before any data exchange takes place. Not only does it confirm that the entity is who they claim to be, but also ensures the rights and privileges tied to their identity are upheld. It’s a powerful tool in maintaining the integrity of our digital space, creating an ecosystem of trust and security.
Digital Signatures
We can take our security protocols to another level with the use of Digital Signatures. Integral to the DoD PKI, digital signatures provide an added layer of authenticity and non-repudiation. When a document is signed digitally, it’s carried out using the private key which is unique to every user.
This digital signature not only confirms the identity of the sender but also ensures the source document has not been tampered with after signing. So, if any alterations are made, the signature becomes invalid, marking the document as compromised.
Using the DoD Public Key, maintaining an airtight security circle is more manageable. It bolsters the trust within the network, delineates our digital spaces, and creates a heightened sense of security while communicating or performing transactions.
As technology advances, we need to understand and harness these advantages with the sophistication they require. In understanding the benefits, we can optimize our systems to better cater to our security needs, fostering a reliable and secure digital environment.